A better way to control your network:
Cisco DNA Center is the network management and command center for Cisco DNA, intent-based network for the enterprise.
Intent-based networking is a big push for the future of network management.
**Prerequisites notes:
**1. VM or customer UCS server is NOT supported
2. IP addresses:
- DNS server (2+ recommended)
- NTP server (2+ recommended)
- Proxy Server IP address and port (http proxy only)
3. Subnets:
- /21 Cluster subnet
- /21 Services subnet
- (RFC1918 - internal subnets, should not be routable, for internal use)
Ports:
- CIMC
- Enterprise Network (to talk with network devices/push config/collect info)
- Intra Cluster Link (for HA, up to 3 DNA). Once DNAC is installed, this IP can NOT be changed - They will all need to connect to switches.
- Management (UI access)
- Cloud Update Connectivity (optional) - optional if Enterprise/Management has access to the Cloud
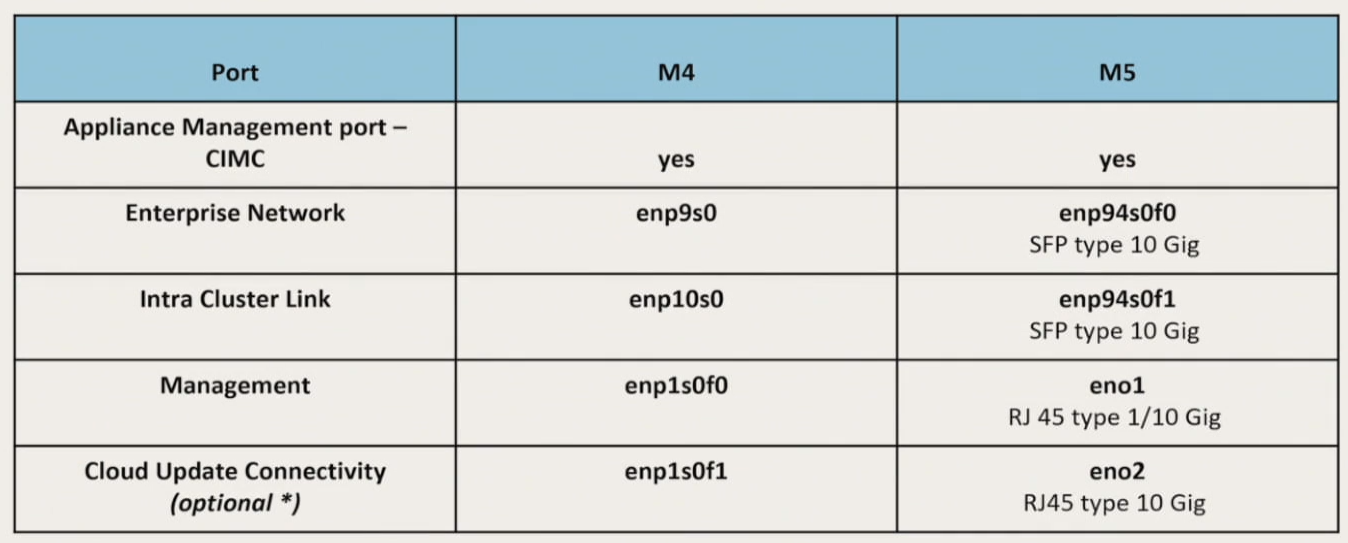
M5:
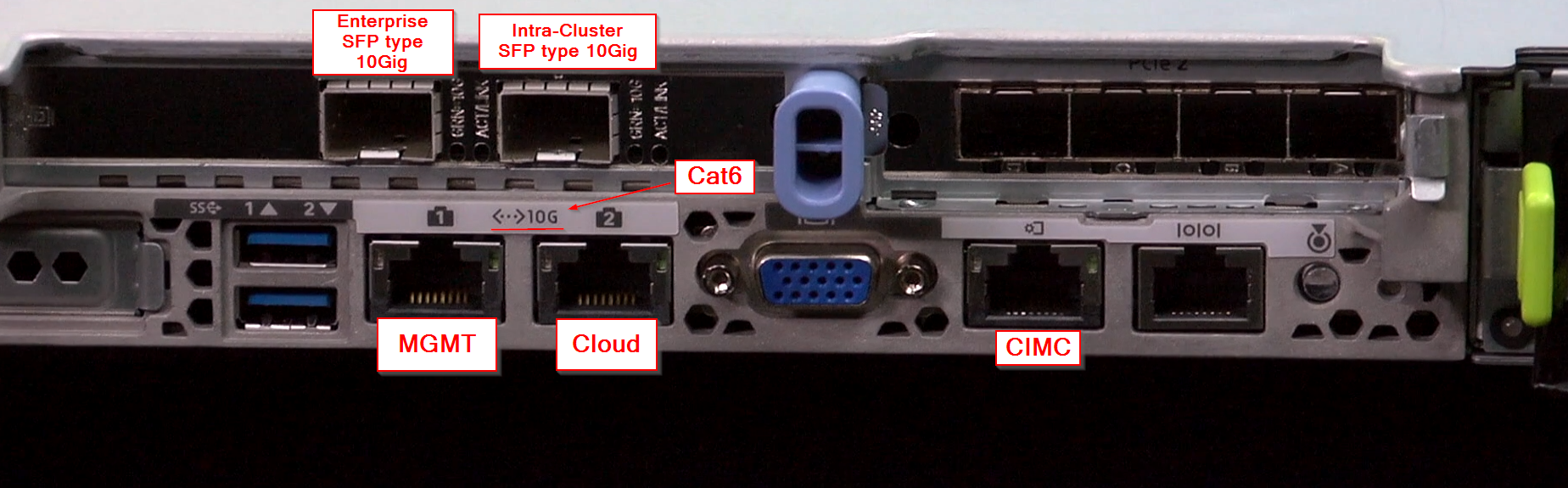
IP addresses:
- Cloud Port Address (Optional): One IP address with subnet mask for the 1Gbps Cloud Port (2, enp1s0f1, Network Adapter 3) - used only when you cannot connect to the cloud using the Enterprise Port. You do not need an IP for the Cloud Port unless you must use it for this purpose
- Cisco DNA Center GUI Port Address (Required): One IP address with subnet mask for the 1Gbps Cisco DNA Center Port (1, enp1s0f0, Network Adapter 2)
- CIMC Port Address (Required): One IP address with subnet mask for the 1Gbps CIMC Port (Port M)
- Enterprise Port Address (Required): One IP address with subnet mask for the 10Gbps Enterprise Port (Port 1, enp9s0, Network Adapter 4)
- Cluster Port Address (Required): One IP address with subnet mask for the 10Gbps Cluster Port (Port 2, enp10so, Network Adapter 1)
URL that needs to be reachable from the DNA Center:
- DNA Center Update package downloads: https://*.ciscoconnectdna.com/*
- Smart Account and SWIM Software Downloads: https://*.cisco.com/*
- Rendering Geo-Maps on the DNA Center UI: https://*.tiles.mapbox.com/*
- User feedback: https://dnacenter.uservoice.com/
Passwords:
- Linux CLI password
- Administartor password for GUI
Time to install: about 1 hour
Option: download ISO, burn ISO to USB(45min) using Etcher tool on Win10 PC, boot DNAC from USB and cluster/Join a cluster (3-4 hours)
ISO download link: https://software.cisco.com/download/specialrelease/cad2074306476371efeea98bf78dc744
Check DNAC installation:
1. $ maglev package status -> everything should be Deployed or Not Deployed if some modules have not been installed, but once installed - everything should be Deployed
2. $ magctl node status -> make sure there are no errors
3. $ magctl service nodescale progress -> all need to be SUCCESS
During the initial setup:
1. Change admin password (could be skipped)
2. CCO account for Cisco.com
3. CCO for Smart Account
4 Proxy server (could be skipeed)
note: Must to access Terms, it enabled Telementy Collection, but later on there is an option (under Settings) to disable Telementy Collection.